Linkwarden
Setup your own Linkwarden Libary. Full Guide including all Information about Browserextension etc.
- Getting Started
- Overview Linkwarden Features & Key Concepts
- Step-by-Step Install Guide for Linkwarden with Traefik on Docker Swarm
- Configuration
- Addons
Getting Started
Overview Linkwarden Features & Key Concepts

 Live-Demo
Live-Demo
Introduction
Linkwarden is a self-hosted, open-source bookmark manager designed to help individuals and teams collect, organize, and preserve web content. It not only functions as a tool to save and categorize important links but also ensures that the content remains accessible even if the original webpage is no longer available. By automatically saving web pages as screenshots, PDFs, and HTML files, Linkwarden combats the issue of "link rot"—the phenomenon where useful webpages disappear or change over time.
Designed with collaboration in mind, Linkwarden allows multiple users to share and work together on collections of bookmarks. It offers seamless integration with services like the Wayback Machine, and for larger organizations, it provides SSO (Single Sign-On) support and various enterprise-level features.
Features
- 📸 Auto capture a screenshot, PDF, single html file, and readable view of each webpage.
- 🏛️ Send your webpage to Wayback Machine (archive.org) for a snapshot. (Optional)
- 📂 Organize links by collection, sub-collection, name, description and multiple tags.
- 👥 Collaborate on gathering links in a collection.
- 🎛️ Customize the permissions of each member.
- 🌐 Share your collected links and preserved formats with the world.
- 📌 Pin your favorite links to dashboard.
- 🔍 Full text search, filter and sort for easy retrieval.
- 📱 Responsive design and supports most modern browsers.
- 🌓 Dark/Light mode support.
- 🧩 Browser extension, managed by the community. Star it here!
- ⬇️ Import and export your bookmarks.
- 🔐 SSO integration. (Enterprise and Self-hosted users only)
- 📦 Installable Progressive Web App (PWA).
- 🍏 iOS and MacOS Apps, maintained by JGeek00.
- 🍎 iOS Shortcut to save links to Linkwarden.
- 🔑 API keys.
- ✅ Bulk actions.
- 👥 User administration.
- 🌐 Support for Other Languages (i18n).
- 📁 Image and PDF Uploads.
- ✨ And many more features. (Literally!)
Public Roadmap
Key Concepts
-
Bookmark Preservation: Linkwarden ensures that your bookmarked webpages remain accessible even if the original content is removed or altered. The tool automatically saves copies in multiple formats such as screenshots and PDFs.
-
Collaborative Bookmarking: Designed for teamwork, Linkwarden allows multiple users to organize and manage collections of bookmarks. This is particularly useful for research projects, group work, or knowledge-sharing within organizations.
-
Flexible Organization: Users can create collections, sub-collections, and assign tags to bookmarks, making it easy to categorize and retrieve relevant links quickly.
-
API and Automation: Linkwarden supports API key generation, enabling users to integrate it with other tools or automate processes like bulk bookmarking or custom searches.
-
Multi-Platform Accessibility: With its responsive design, Linkwarden works across desktop, mobile, and tablet devices. It also offers browser extensions and a Progressive Web App for added convenience.
-
Security and Privacy: Linkwarden provides security features such as Single Sign-On (SSO) for enterprise users, ensuring secure access to sensitive information.
Conclusion
Linkwarden is a versatile, self-hosted solution for managing bookmarks with a focus on collaboration, preservation, and accessibility. Whether you’re an individual wanting to keep your personal reading list organized or a team collaborating on a project, Linkwarden offers the tools you need to save, categorize, and share web content efficiently. The combination of advanced features like API support, SSO, and automated preservation mechanisms makes it a powerful tool for users who need more than just a standard bookmark manager.
By supporting multiple platforms, offering collaboration features, and ensuring security through privacy-focused options, Linkwarden is an excellent choice for both personal use and enterprise-level teams.
Step-by-Step Install Guide for Linkwarden with Traefik on Docker Swarm
 Introduction
Introduction
In this guide, we'll walk through the process of installing Linkwarden, a self-hosted bookmark manager, on Docker Swarm. This installation will include setting up Traefik as the reverse proxy and configuring persistent storage using GlusterFS. Additionally, we'll cover how to securely set up environment variables, such as the NEXTAUTH_SECRET, and ensure proper file permissions using a custom Linux user.
Step 1: Create a User for Linkwarden Folders
To ensure that only one Linux user has the necessary rights for the Linkwarden folders, we'll create a custom user and group called linkwardenuser. This user will not have a home directory, and the shell will be set to /usr/sbin/nologin for security purposes.
-
Create the custom user and group with the GID and UID set to 10002:
sudo groupadd -g 10002 linkwardenuser sudo useradd -u 10002 -g linkwardenuser -s /usr/sbin/nologin -M linkwardenuser- The
-s /usr/sbin/nologinoption ensures that this user cannot log in interactively, which is a security best practice for service users. - The
-Moption prevents the creation of a home directory, as this user will only be managing Linkwarden's folder permissions and not need a home directory for other purposes.
- The
Step 2: Create Folders for Linkwarden
Next, we’ll create the necessary folders to store Linkwarden’s data on the GlusterFS mount.
-
Create the folders for Linkwarden's data:
mkdir -p /mnt/glustermount/data/linkwarden_data mkdir -p /mnt/glustermount/data/linkwarden_data/pgdata mkdir -p /mnt/glustermount/data/linkwarden_data/lwdata mkdir -p /mnt/glustermount/data/linkwarden_data/storage - Adjust ownership of these folders to the
linkwardenuser, ensuring all files inside are accessible to this user:
This ensures that only thelinkwardenuserhas access to these folders and files, maintaining data security.
sudo chown -R linkwardenuser:linkwardenuser /mnt/glustermount/data/linkwarden_data - Permissions: The following permissions ensure that the owner (user
10002) has full access (read, write, execute) to the directories and files, and that no one else can modify the files.
sudo chmod -R 750 /mnt/glustermount/data/linkwarden_data750 means:
- 7: Owner (user 10002) has read, write, and execute permissions.
- 5: Group has read and execute permissions (but not write).
- 0: Others have no permissions.
Step 3: Create docker-compose.yaml
Now, we’ll create the Docker Compose file that will define two services: one for Linkwarden and another for its PostgreSQL database. We will also configure Traefik to route traffic to Linkwarden.
To Configure the Composefile check out the ENVIROMENT-VARIABLES Wiki Article.
version: "3.5"
services:
linkwarden:
image: ghcr.io/linkwarden/linkwarden:latest
environment:
- DATABASE_URL=postgresql://linkwarden:${POSTGRES_PASSWORD}@postgres:5432/linkwardendb
- NEXTAUTH_URL=http://localhost:3000/api/v1/auth
- NEXTAUTH_SECRET=${NEXTAUTH_SECRET}
- STORAGE_FOLDER=/mnt/glustermount/data/linkwarden_data/storage
- NEXT_PUBLIC_EMAIL_PROVIDER=${NEXT_PUBLIC_EMAIL_PROVIDER}
- EMAIL_FROM=${EMAIL_FROM}
- EMAIL_SERVER=${EMAIL_SERVER}
- BASE_URL=${BASE_URL}
- TZ=Europe/Zurich
- GID=10002
- UID=10002
restart: always
ports:
- 3000:3000
volumes:
- /mnt/glustermount/data/linkwarden_data/lwdata:/data/data
depends_on:
- postgres
networks:
- management_net
deploy:
replicas: 1
placement:
constraints:
- node.role == manager
labels:
- "traefik.enable=true"
- "traefik.http.routers.linkwarden.rule=Host(`linkwarden.domain.tld`)"
- "traefik.http.services.linkwarden.loadbalancer.server.port=3000"
- "traefik.http.routers.linkwarden.entrypoints=websecure"
- "traefik.http.routers.linkwarden.tls.certresolver=leresolver"
postgres:
image: postgres:16-alpine
environment:
POSTGRES_USER: linkwarden
POSTGRES_PASSWORD: ${POSTGRES_PASSWORD}
POSTGRES_DB: linkwardendb
TZ: Europe/Zurich
GID: 10002
UID: 10002
restart: always
volumes:
- /mnt/glustermount/data/linkwarden_data/pgdata:/var/lib/postgresql/data
ports:
- 5432:5432
networks:
- management_net
deploy:
replicas: 1
placement:
constraints:
- node.role == manager
labels:
- "traefik.enable=true"
- "traefik.http.services.postgres.loadbalancer.server.port=5432"
networks:
management_net:
external: true
SMTP Settings
- # The base URL of your Linkwarden installation (replace with your domain or local IP)
BASE_URL=https://linkwarden.domain.tld - # Email provider for sending notification emails (example: SMTP settings)
NEXT_PUBLIC_EMAIL_PROVIDER=smtp - # Email address that Linkwarden will use to send emails from (replace with your actual email)
EMAIL_FROM=linkwarden@domain.tld - # SMTP server details (example: for Gmail's SMTP server)
EMAIL_SERVER=smtp://smtp.gmail.com:587
Step 4: Create the NEXTAUTH_SECRET
The NEXTAUTH_SECRET is used to sign authentication tokens securely. You need to generate a random string to be used as the NEXTAUTH_SECRET.
You can generate a secure NEXTAUTH_SECRET using the following command:
openssl rand -base64 32This command will generate a 32-byte random string that you can add to your .env file as the NEXTAUTH_SECRET.
What Does NEXTAUTH_SECRET Do?
The NEXTAUTH_SECRET is critical for securing the authentication process in Linkwarden. It is used to sign and encrypt tokens, ensuring that user sessions are protected from tampering or unauthorized access.
Step 5: Start the Stack
Once everything is configured, you can start the Linkwarden stack either manually or through Portainer.
Start with Docker Swarm
To start the stack manually, run:
docker stack deploy -c docker-compose.yaml linkwardenStart with Portainer
Alternatively, you can use Portainer’s graphical interface to import the docker-compose.yaml file and start the stack.
Once the stack is deployed, Linkwarden will be available at https://linkwarden.domain.tld (or whatever domain you've configured).
Conclusion
This guide provides a detailed walkthrough for setting up Linkwarden with Traefik on Docker Swarm. From user and folder management to Docker Compose configuration, these steps ensure a secure and scalable deployment of your self-hosted bookmark manager.
Configuration
Enviroment Variables List
Environment Variables
Here are all the additional variables you can define in the .env file for setting up a self-hosted instance:
| Environment Variable | Default | Description |
|---|---|---|
| PAGINATION_TAKE_COUNT | 50 | The numbers of Links to fetch every time you reach the bottom of the webpage |
| STORAGE_FOLDER | /data | The folder to store your Screenshots, PDFs, and profile photos. |
| AUTOSCROLL_TIMEOUT | 30 | The amount of time to wait for the website to be archived (in seconds). |
| RE_ARCHIVE_LIMIT | 5 | Adjusts how often a user can trigger a new archive for each link (in minutes). |
Authentication Settings
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_DISABLE_REGISTRATION | false | If set to true, registration will be disabled. |
| NEXT_PUBLIC_CREDENTIALS_ENABLED | true | If set to true, users will be able to login with username and password. |
| DISABLE_NEW_SSO_USERS | false | If set to true, new users will not be able to login with SSO. |
Digital Ocean Spaces/AWS S3 Settings
Digital Ocean Spaces uses AWS S3 behind the scenes, so you can also choose to store your STORAGE_FOLDER files in Digital Ocean Spaces or Amazon S3:
| Environment Variable | Default | Description |
|---|---|---|
| SPACES_KEY | - | - |
| SPACES_SECRET | - | - |
| SPACES_ENDPOINT | - | - |
| SPACES_BUCKET_NAME | - | - |
| SPACES_REGION | - | - |
| SPACES_FORCE_PATH_STYLE | - | - |
SMTP Settings
The variables you need to configure to enable password recovery without the admin interfering, email verification, etc...
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_EMAIL_PROVIDER | - | If set to true, email will be enabled and you'll need to define the next two variables below. |
| EMAIL_FROM | - | The email that will send the verification emails. |
| EMAIL_SERVER | - | That sensitive string that starts with smtp://... . |
Full EnviromentVariables List
Core Configuration:
-
NEXTAUTH_URL: The URL for NextAuth (authentication).
Example:NEXTAUTH_URL=http://localhost:3000/api/v1/auth -
NEXTAUTH_SECRET: Secret key for signing NextAuth tokens.
Example:NEXTAUTH_SECRET=supersecretkey -
DATABASE_URL: PostgreSQL database connection string.
Example:DATABASE_URL=postgresql://linkwarden:password@localhost:5432/linkwardendb -
POSTGRES_PASSWORD: Password for the PostgreSQL database user.
Example:POSTGRES_PASSWORD=yourpassword
Optional Settings:
-
PAGINATION_TAKE_COUNT: Number of links displayed per page.
Example:PAGINATION_TAKE_COUNT=20 -
STORAGE_FOLDER: Directory path for storing files like images and PDFs.
Example:STORAGE_FOLDER=/mnt/data/linkwarden_storage -
AUTOSCROLL_TIMEOUT: Time (in ms) before auto-scroll happens.
Example:AUTOSCROLL_TIMEOUT=5000 -
NEXT_PUBLIC_DISABLE_REGISTRATION: Disable user registration if
true.
Example:NEXT_PUBLIC_DISABLE_REGISTRATION=true -
NEXT_PUBLIC_CREDENTIALS_ENABLED: Enable login with username/password.
Example:NEXT_PUBLIC_CREDENTIALS_ENABLED=true -
DISABLE_NEW_SSO_USERS: Disable new users signing up via SSO.
Example:DISABLE_NEW_SSO_USERS=true -
RE_ARCHIVE_LIMIT: Maximum number of links to re-archive.
Example:RE_ARCHIVE_LIMIT=50 -
MAX_LINKS_PER_USER: Max number of links a user can save.
Example:MAX_LINKS_PER_USER=1000 -
ARCHIVE_TAKE_COUNT: Number of links to archive in one operation.
Example:ARCHIVE_TAKE_COUNT=100 -
BROWSER_TIMEOUT: Browser process timeout (in ms).
Example:BROWSER_TIMEOUT=30000 -
IGNORE_UNAUTHORIZED_CA: Ignore unauthorized SSL certificates.
Example:IGNORE_UNAUTHORIZED_CA=true -
IGNORE_HTTPS_ERRORS: Ignore HTTPS-related errors.
Example:IGNORE_HTTPS_ERRORS=true -
IGNORE_URL_SIZE_LIMIT: Ignore URL size limits.
Example:IGNORE_URL_SIZE_LIMIT=true -
NEXT_PUBLIC_DEMO: Enable demo mode.
Example:NEXT_PUBLIC_DEMO=true -
NEXT_PUBLIC_DEMO_USERNAME: Demo mode username.
Example:NEXT_PUBLIC_DEMO_USERNAME=demo -
NEXT_PUBLIC_DEMO_PASSWORD: Demo mode password.
Example:NEXT_PUBLIC_DEMO_PASSWORD=demopassword -
NEXT_PUBLIC_ADMIN: Admin username.
Example:NEXT_PUBLIC_ADMIN=adminuser -
NEXT_PUBLIC_MAX_FILE_BUFFER: Max buffer size for file uploads.
Example:NEXT_PUBLIC_MAX_FILE_BUFFER=1024 -
MONOLITH_MAX_BUFFER: Max buffer size for Monolith operations.
Example:MONOLITH_MAX_BUFFER=2048 -
MONOLITH_CUSTOM_OPTIONS: Custom options for Monolith (web archiving).
Example:MONOLITH_CUSTOM_OPTIONS="--timeout 60000" -
PDF_MAX_BUFFER: Max buffer size for PDF processing.
Example:PDF_MAX_BUFFER=4096 -
SCREENSHOT_MAX_BUFFER: Max buffer size for screenshots.
Example:SCREENSHOT_MAX_BUFFER=2048 -
READABILITY_MAX_BUFFER: Max buffer size for readability processing.
Example:READABILITY_MAX_BUFFER=1024 -
PREVIEW_MAX_BUFFER: Max buffer size for preview generation.
Example:PREVIEW_MAX_BUFFER=2048 -
IMPORT_LIMIT: Limit on the number of links for import.
Example:IMPORT_LIMIT=500
AWS S3 Settings:
-
SPACES_KEY: AWS S3 access key.
Example:SPACES_KEY=yourawskey -
SPACES_SECRET: AWS S3 secret key.
Example:SPACES_SECRET=yourawssecret -
SPACES_ENDPOINT: AWS S3 endpoint URL.
Example:SPACES_ENDPOINT=https://nyc3.digitaloceanspaces.com -
SPACES_BUCKET_NAME: Name of the S3 bucket.
Example:SPACES_BUCKET_NAME=mybucket -
SPACES_REGION: AWS region for S3.
Example:SPACES_REGION=us-east-1 -
SPACES_FORCE_PATH_STYLE: Force path-style access for S3.
Example:SPACES_FORCE_PATH_STYLE=true
SMTP Settings:
-
NEXT_PUBLIC_EMAIL_PROVIDER: Email provider (e.g., SMTP).
Example:NEXT_PUBLIC_EMAIL_PROVIDER=smtp -
EMAIL_FROM: Email address from which emails are sent.
Example:EMAIL_FROM=no-reply@yourdomain.com -
EMAIL_SERVER: SMTP server URL.
Example:EMAIL_SERVER=smtp://smtp.mailtrap.io:2525 -
BASE_URL: The base URL of your application.
Example:BASE_URL=https://app.yourdomain.com
Proxy Settings:
-
PROXY: Proxy server URL.
Example:PROXY=http://proxy.yourdomain.com -
PROXY_USERNAME: Username for proxy authentication.
Example:PROXY_USERNAME=proxyuser -
PROXY_PASSWORD: Password for proxy authentication.
Example:PROXY_PASSWORD=proxypassword -
PROXY_BYPASS: Hosts to bypass the proxy.
Example:PROXY_BYPASS=localhost,127.0.0.1
PDF Archive Settings:
-
PDF_MARGIN_TOP: Top margin for PDFs.
Example:PDF_MARGIN_TOP=10 -
PDF_MARGIN_BOTTOM: Bottom margin for PDFs.
Example:PDF_MARGIN_BOTTOM=10
SSO Providers:
# 42 School
NEXT_PUBLIC_FORTYTWO_ENABLED=
FORTYTWO_CUSTOM_NAME=
FORTYTWO_CLIENT_ID=
FORTYTWO_CLIENT_SECRET=
# Apple
NEXT_PUBLIC_APPLE_ENABLED=
APPLE_CUSTOM_NAME=
APPLE_ID=
APPLE_SECRET=
# Atlassian
NEXT_PUBLIC_ATLASSIAN_ENABLED=
ATLASSIAN_CUSTOM_NAME=
ATLASSIAN_CLIENT_ID=
ATLASSIAN_CLIENT_SECRET=
ATLASSIAN_SCOPE=
# Auth0
NEXT_PUBLIC_AUTH0_ENABLED=
AUTH0_CUSTOM_NAME=
AUTH0_ISSUER=
AUTH0_CLIENT_SECRET=
AUTH0_CLIENT_ID=
# Authelia
NEXT_PUBLIC_AUTHELIA_ENABLED=""
AUTHELIA_CLIENT_ID=""
AUTHELIA_CLIENT_SECRET=""
AUTHELIA_WELLKNOWN_URL=""
# Authentik
NEXT_PUBLIC_AUTHENTIK_ENABLED=
AUTHENTIK_CUSTOM_NAME=
AUTHENTIK_ISSUER=
AUTHENTIK_CLIENT_ID=
AUTHENTIK_CLIENT_SECRET=
# Azure AD B2C
NEXT_PUBLIC_AZURE_AD_B2C_ENABLED=
AZURE_AD_B2C_TENANT_NAME=
AZURE_AD_B2C_CLIENT_ID=
AZURE_AD_B2C_CLIENT_SECRET=
AZURE_AD_B2C_PRIMARY_USER_FLOW=
# Azure AD
NEXT_PUBLIC_AZURE_AD_ENABLED=
AZURE_AD_CLIENT_ID=
AZURE_AD_CLIENT_SECRET=
AZURE_AD_TENANT_ID=
# Battle.net
NEXT_PUBLIC_BATTLENET_ENABLED=
BATTLENET_CUSTOM_NAME=
BATTLENET_CLIENT_ID=
BATTLENET_CLIENT_SECRET=
BATTLENET_ISSUER=
# Box
NEXT_PUBLIC_BOX_ENABLED=
BOX_CUSTOM_NAME=
BOX_CLIENT_ID=
BOX_CLIENT_SECRET=
# Bungie
NEXT_PUBLIC_BUNGIE_ENABLED=
BUNGIE_CUSTOM_NAME=
BUNGIE_CLIENT_ID=
BUNGIE_CLIENT_SECRET=
BUNGIE_API_KEY=
# Cognito
NEXT_PUBLIC_COGNITO_ENABLED=
COGNITO_CUSTOM_NAME=
COGNITO_CLIENT_ID=
COGNITO_CLIENT_SECRET=
COGNITO_ISSUER=
# Coinbase
NEXT_PUBLIC_COINBASE_ENABLED=
COINBASE_CUSTOM_NAME=
COINBASE_CLIENT_ID=
COINBASE_CLIENT_SECRET=
# Discord
NEXT_PUBLIC_DISCORD_ENABLED=
DISCORD_CUSTOM_NAME=
DISCORD_CLIENT_ID=
DISCORD_CLIENT_SECRET=
# Dropbox
NEXT_PUBLIC_DROPBOX_ENABLED=
DROPBOX_CUSTOM_NAME=
DROPBOX_CLIENT_ID=
DROPBOX_CLIENT_SECRET=
# DuendeIndentityServer6
NEXT_PUBLIC_DUENDE_IDS6_ENABLED=
DUENDE_IDS6_CUSTOM_NAME=
DUENDE_IDS6_CLIENT_ID=
DUENDE_IDS6_CLIENT_SECRET=
DUENDE_IDS6_ISSUER=
# EVE Online
NEXT_PUBLIC_EVEONLINE_ENABLED=
EVEONLINE_CUSTOM_NAME=
EVEONLINE_CLIENT_ID=
EVEONLINE_CLIENT_SECRET=
# Facebook
NEXT_PUBLIC_FACEBOOK_ENABLED=
FACEBOOK_CUSTOM_NAME=
FACEBOOK_CLIENT_ID=
FACEBOOK_CLIENT_SECRET=
# FACEIT
NEXT_PUBLIC_FACEIT_ENABLED=
FACEIT_CUSTOM_NAME=
FACEIT_CLIENT_ID=
FACEIT_CLIENT_SECRET=
# Foursquare
NEXT_PUBLIC_FOURSQUARE_ENABLED=
FOURSQUARE_CUSTOM_NAME=
FOURSQUARE_CLIENT_ID=
FOURSQUARE_CLIENT_SECRET=
FOURSQUARE_APIVERSION=
# Freshbooks
NEXT_PUBLIC_FRESHBOOKS_ENABLED=
FRESHBOOKS_CUSTOM_NAME=
FRESHBOOKS_CLIENT_ID=
FRESHBOOKS_CLIENT_SECRET=
# FusionAuth
NEXT_PUBLIC_FUSIONAUTH_ENABLED=
FUSIONAUTH_CUSTOM_NAME=
FUSIONAUTH_CLIENT_ID=
FUSIONAUTH_CLIENT_SECRET=
FUSIONAUTH_ISSUER=
FUSIONAUTH_TENANT_ID=
# GitHub
NEXT_PUBLIC_GITHUB_ENABLED=
GITHUB_CUSTOM_NAME=
GITHUB_ID=
GITHUB_SECRET=
# GitLab
NEXT_PUBLIC_GITLAB_ENABLED=
GITLAB_CUSTOM_NAME=
GITLAB_CLIENT_ID=
GITLAB_CLIENT_SECRET=
# Google
NEXT_PUBLIC_GOOGLE_ENABLED=
GOOGLE_CUSTOM_NAME=
GOOGLE_CLIENT_ID=
GOOGLE_CLIENT_SECRET=
# HubSpot
NEXT_PUBLIC_HUBSPOT_ENABLED=
HUBSPOT_CUSTOM_NAME=
HUBSPOT_CLIENT_ID=
HUBSPOT_CLIENT_SECRET=
# IdentityServer4
NEXT_PUBLIC_IDS4_ENABLED=
IDS4_CUSTOM_NAME=
IDS4_CLIENT_ID=
IDS4_CLIENT_SECRET=
IDS4_ISSUER=
# Kakao
NEXT_PUBLIC_KAKAO_ENABLED=
KAKAO_CUSTOM_NAME=
KAKAO_CLIENT_ID=
KAKAO_CLIENT_SECRET=
# Keycloak
NEXT_PUBLIC_KEYCLOAK_ENABLED=
KEYCLOAK_CUSTOM_NAME=
KEYCLOAK_ISSUER=
KEYCLOAK_CLIENT_ID=
KEYCLOAK_CLIENT_SECRET=
# LINE
NEXT_PUBLIC_LINE_ENABLED=
LINE_CUSTOM_NAME=
LINE_CLIENT_ID=
LINE_CLIENT_SECRET=
# LinkedIn
NEXT_PUBLIC_LINKEDIN_ENABLED=
LINKEDIN_CUSTOM_NAME=
LINKEDIN_CLIENT_ID=
LINKEDIN_CLIENT_SECRET=
# Mailchimp
NEXT_PUBLIC_MAILCHIMP_ENABLED=
MAILCHIMP_CUSTOM_NAME=
MAILCHIMP_CLIENT_ID=
MAILCHIMP_CLIENT_SECRET=
# Mail.ru
NEXT_PUBLIC_MAILRU_ENABLED=
MAILRU_CUSTOM_NAME=
MAILRU_CLIENT_ID=
MAILRU_CLIENT_SECRET=
# Naver
NEXT_PUBLIC_NAVER_ENABLED=
NAVER_CUSTOM_NAME=
NAVER_CLIENT_ID=
NAVER_CLIENT_SECRET=
# Netlify
NEXT_PUBLIC_NETLIFY_ENABLED=
NETLIFY_CUSTOM_NAME=
NETLIFY_CLIENT_ID=
NETLIFY_CLIENT_SECRET=
# Okta
NEXT_PUBLIC_OKTA_ENABLED=
OKTA_CUSTOM_NAME=
OKTA_CLIENT_ID=
OKTA_CLIENT_SECRET=
OKTA_ISSUER=
# OneLogin
NEXT_PUBLIC_ONELOGIN_ENABLED=
ONELOGIN_CUSTOM_NAME=
ONELOGIN_CLIENT_ID=
ONELOGIN_CLIENT_SECRET=
ONELOGIN_ISSUER=
# Osso
NEXT_PUBLIC_OSSO_ENABLED=
OSSO_CUSTOM_NAME=
OSSO_CLIENT_ID=
OSSO_CLIENT_SECRET=
OSSO_ISSUER=
# osu!
NEXT_PUBLIC_OSU_ENABLED=
OSU_CUSTOM_NAME=
OSU_CLIENT_ID=
OSU_CLIENT_SECRET=
# Patreon
NEXT_PUBLIC_PATREON_ENABLED=
PATREON_CUSTOM_NAME=
PATREON_CLIENT_ID=
PATREON_CLIENT_SECRET=
# Pinterest
NEXT_PUBLIC_PINTEREST_ENABLED=
PINTEREST_CUSTOM_NAME=
PINTEREST_CLIENT_ID=
PINTEREST_CLIENT_SECRET=
# Pipedrive
NEXT_PUBLIC_PIPEDRIVE_ENABLED=
PIPEDRIVE_CUSTOM_NAME=
PIPEDRIVE_CLIENT_ID=
PIPEDRIVE_CLIENT_SECRET=
# Reddit
NEXT_PUBLIC_REDDIT_ENABLED=
REDDIT_CUSTOM_NAME=
REDDIT_CLIENT_ID=
REDDIT_CLIENT_SECRET=
# Salesforce
NEXT_PUBLIC_SALESFORCE_ENABLED=
SALESFORCE_CUSTOM_NAME=
SALESFORCE_CLIENT_ID=
SALESFORCE_CLIENT_SECRET=
# Slack
NEXT_PUBLIC_SLACK_ENABLED=
SLACK_CUSTOM_NAME=
SLACK_CLIENT_ID=
SLACK_CLIENT_SECRET=
# Spotify
NEXT_PUBLIC_SPOTIFY_ENABLED=
SPOTIFY_CUSTOM_NAME=
SPOTIFY_CLIENT_ID=
SPOTIFY_CLIENT_SECRET=
# Strava
NEXT_PUBLIC_STRAVA_ENABLED=
STRAVA_CUSTOM_NAME=
STRAVA_CLIENT_ID=
STRAVA_CLIENT_SECRET=
# Todoist
NEXT_PUBLIC_TODOIST_ENABLED=
TODOIST_CUSTOM_NAME=
TODOIST_CLIENT_ID=
TODOIST_CLIENT_SECRET=
# Twitch
NEXT_PUBLIC_TWITCH_ENABLED=
TWITCH_CUSTOM_NAME=
TWITCH_CLIENT_ID=
TWITCH_CLIENT_SECRET=
# United Effects
NEXT_PUBLIC_UNITED_EFFECTS_ENABLED=
UNITED_EFFECTS_CUSTOM_NAME=
UNITED_EFFECTS_CLIENT_ID=
UNITED_EFFECTS_CLIENT_SECRET=
UNITED_EFFECTS_ISSUER=
# VK
NEXT_PUBLIC_VK_ENABLED=
VK_CUSTOM_NAME=
VK_CLIENT_ID=
VK_CLIENT_SECRET=
# Wikimedia
NEXT_PUBLIC_WIKIMEDIA_ENABLED=
WIKIMEDIA_CUSTOM_NAME=
WIKIMEDIA_CLIENT_ID=
WIKIMEDIA_CLIENT_SECRET=
# Wordpress.com
NEXT_PUBLIC_WORDPRESS_ENABLED=
WORDPRESS_CUSTOM_NAME=
WORDPRESS_CLIENT_ID=
WORDPRESS_CLIENT_SECRET=
# Yandex
NEXT_PUBLIC_YANDEX_ENABLED=
YANDEX_CUSTOM_NAME=
YANDEX_CLIENT_ID=
YANDEX_CLIENT_SECRET=
# Zitadel
NEXT_PUBLIC_ZITADEL_ENABLED=
ZITADEL_CUSTOM_NAME=
ZITADEL_CLIENT_ID=
ZITADEL_CLIENT_SECRET=
ZITADEL_ISSUER=
# Zoho
NEXT_PUBLIC_ZOHO_ENABLED=
ZOHO_CUSTOM_NAME=
ZOHO_CLIENT_ID=
ZOHO_CLIENT_SECRET=
# Zoom
NEXT_PUBLIC_ZOOM_ENABLED=
ZOOM_CUSTOM_NAME=
ZOOM_CLIENT_ID=
ZOOM_CLIENT_SECRET=
Add 3rd Party Authentication (Google, Twitch etc.)
In the Following Wiki Article i will Provide you Informations on how to add SSO API's to your Linkwarden.
Here are all the SSO/OAuth integrations Linkwarden currently has. (10.10.2024)
Other than the Authentik and Keycloak integrations, most of the other integrations are untested. Please first backup your database, just in case.
To get support from the community, please visit our Discord server.
- 42 School
- Apple
- Atlassian
- Auth0
- Authelia
- Authentik
- Battle.net
- Box
- Bungie
- Cognito
- Coinbase
- Discord
- Dropbox
- Duende Identity Server 6
- EVE Online
- Facebook
- FACEIT
- Foursquare
- Freshbooks
- Fusionauth
- Github
- Gitlab
- Google
- Hubspot
- IdentityServer4
- Kakao
- Keycloak
- Line
- Linkedin
- Mailchimp
- Mailru
- Naver
- Netlify
- Okta
- Onelogin
- Osso
- osu!
- Patreon
- Pinterest
- Pipedrive
- Reddit
- Salesforce
- Slack
- Spotify
- Strava
- Todoist
- Twitch
- United Effects
- VK
- Wikimedia
- Wordpress.com
- Yandex
- Zitadel
- Zoho
- Zoom
IMPORTANT
This is the Callback URL for your SSO-API'shttps://domain.tld/api/v1/auth/callback/servicename
For Example:https://links.aeoneros.com/api/v1/auth/callback/discord
42 School
The variables you need to configure to enable support for 42 School (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FORTYTWO_ENABLED | - | If set to true, 42 School will be enabled and you'll need to define the variables below. |
| FORTYTWO_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FORTYTWO_CLIENT_ID | - | Client ID |
| FORTYTWO_CLIENT_SECRET | - | Client Secret. |
Apple
The variables you need to configure to enable support for Apple (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_APPLE_ENABLED | - | If set to true, Apple will be enabled and you'll need to define the variables below. |
| APPLE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| APPLE_CLIENT_ID | - | Client ID |
| APPLE_CLIENT_SECRET | - | Client Secret. |
Atlassian
The variables you need to configure to enable support for Atlassian (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_ATLASSIAN_ENABLED | - | If set to true, Atlassian will be enabled and you'll need to define the variables below. |
| ATLASSIAN_CUSTOM_NAME | - | Optionally set a custom provider name. |
| ATLASSIAN_SCOPE | - | Optionally set a custom scope. |
| ATLASSIAN_CLIENT_ID | - | Client ID |
| ATLASSIAN_CLIENT_SECRET | - | Client Secret. |
Auth0
The variables you need to configure to enable support for Auth0 (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_AUTH0_ENABLED | - | If set to true, Auth0 will be enabled and you'll need to define the variables below. |
| AUTH0_CUSTOM_NAME | - | Optionally set a custom provider name. |
| AUTH0_ISSUER | - | Issuer. |
| AUTH0_CLIENT_ID | - | Client ID |
| AUTH0_CLIENT_SECRET | - | Client Secret. |
Authelia
The variables you need to configure to enable support for Authelia (OIDC).
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_AUTHELIA_ENABLED | - | If set to true, Authelia will be enabled and you'll need to define the variables below. |
| AUTHELIA_WELLKNOWN_URL | - | https://{{authelia.domain.com}}/.well-known/openid-configuration |
| AUTHELIA_CLIENT_ID | - | Client ID |
| AUTHELIA_CLIENT_SECRET | - | Client Secret. (Random Password from command below) |
Generate the client secret with
docker exec -it authelia authelia crypto hash generate pbkdf2 --variant sha512 --random --random.length 72 --random.charset rfc3986
The Random Password should be used for the AUTHELIA_CLIENT_SECRET variable in linkwarden & the Digest should be used for client_secret in th Authelia config below.
Authelia config should be as follows:
- client_id: linkwarden
client_name: Linkwarden
client_secret: {{Digest from command above}}
public: false
authorization_policy: one_factor
consent_mode: implicit
scopes:
- openid
- groups
- email
- profile
redirect_uris:
- https://{{linkwarden.domain.com}}/api/v1/auth/callback/authelia
userinfo_signed_response_alg: none
Authentik
The variables you need to configure to enable support for Authentik (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_AUTHENTIK_ENABLED | - | If set to true, Authentik will be enabled and you'll need to define the variables below. |
| AUTHENTIK_CUSTOM_NAME | - | Optionally set a custom provider name. |
| AUTHENTIK_ISSUER | - | This is the "OpenID Configuration Issuer" shown in the Provider Overview. Note that you must delete the "/" at the end of the URL. Should look like: https://authentik.my-doma.in/application/o/linkwarden |
| AUTHENTIK_CLIENT_ID | - | Client ID copied from the Provider Overview screen in Authentik |
| AUTHENTIK_CLIENT_SECRET | - | Client Secret copied from the Provider Overview screen in Authentik |
Administrators are required to also set the environment variable NEXTAUTH_URL=https://linkwarden.my-doma.in/api/v1/auth (during the linkwarden install process or docker ENV variables) and ensure a JWT signing key is selected in Authentik's Providers settings (this can be the default self-signed authentik certificate). Note that the Authentik Provider "Redirect URIs" section can be left blank, it will autofill with a URL after the first time it is used. The URL will look like: https://linkwarden.my-doma.in/api/v1/auth/callback/authentik
Authentik Setup Example:
Create a Provider on Authentik with the following settings:
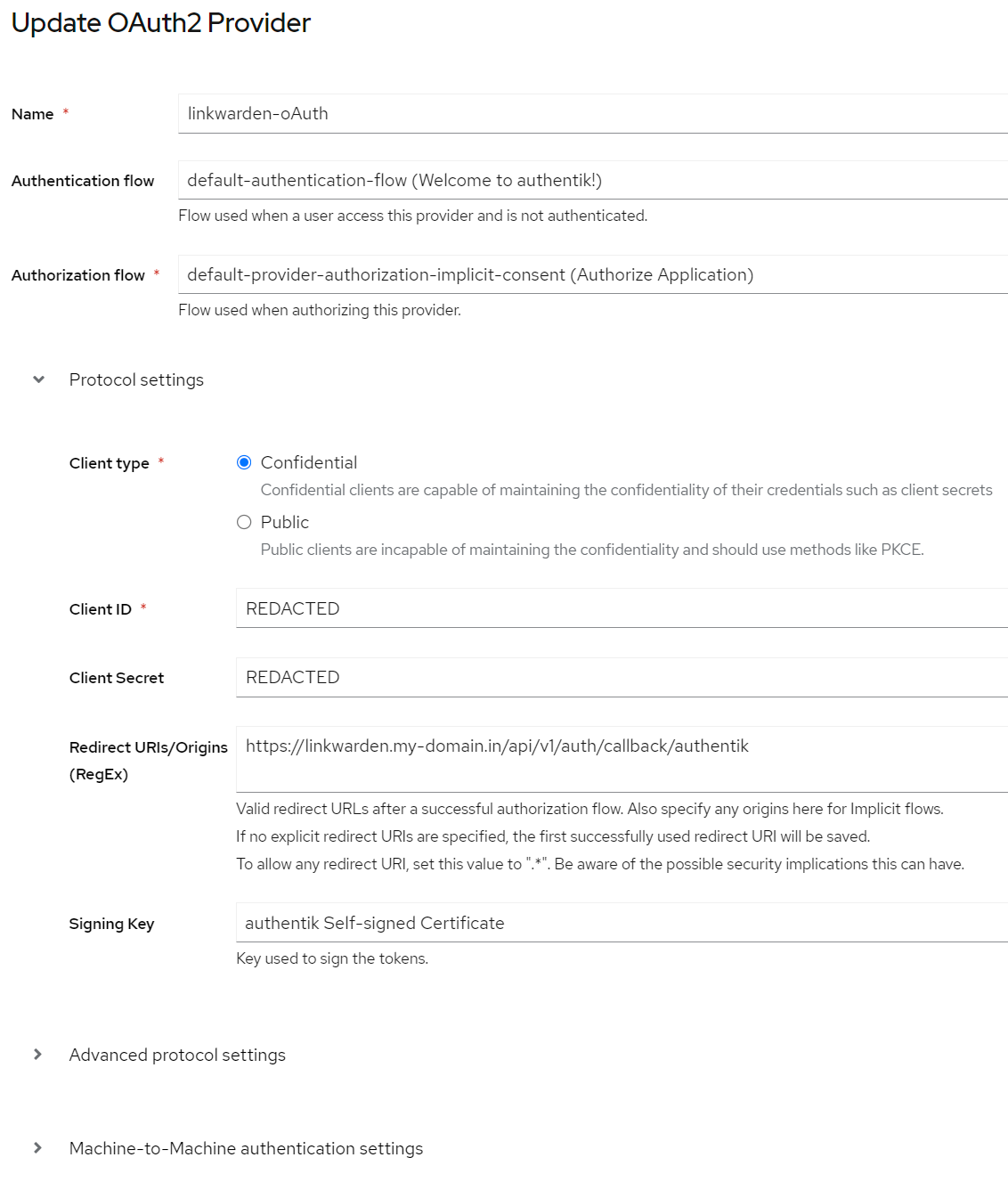
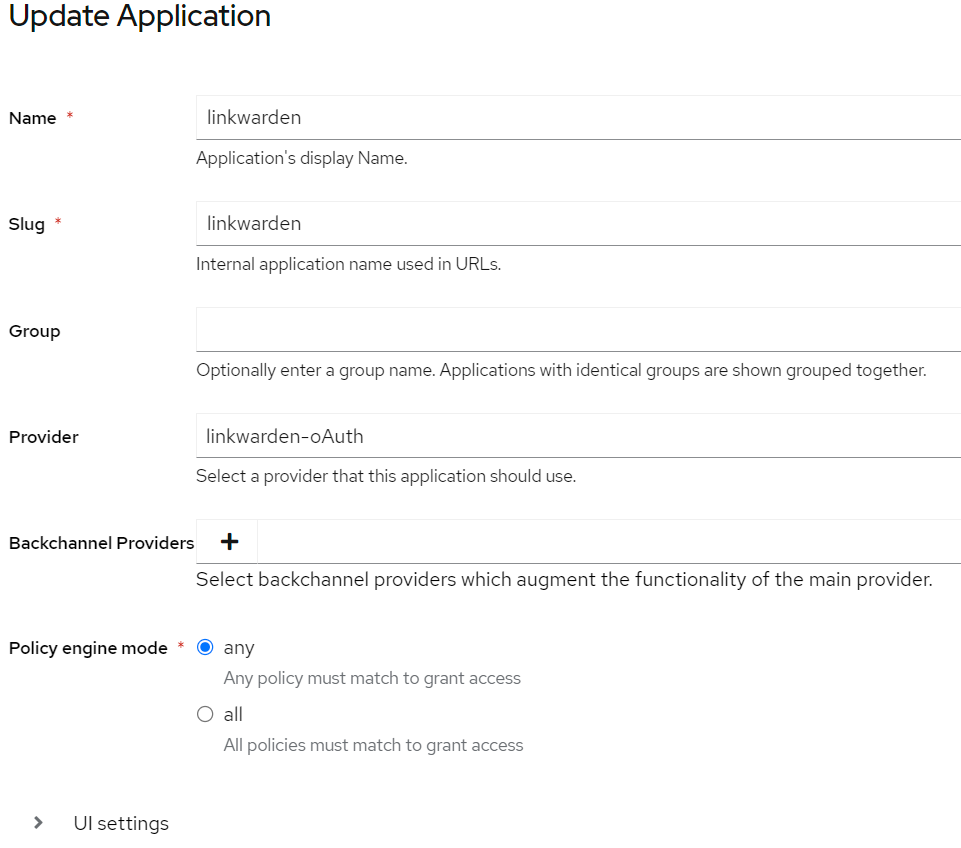
Create an Application with the following settings:
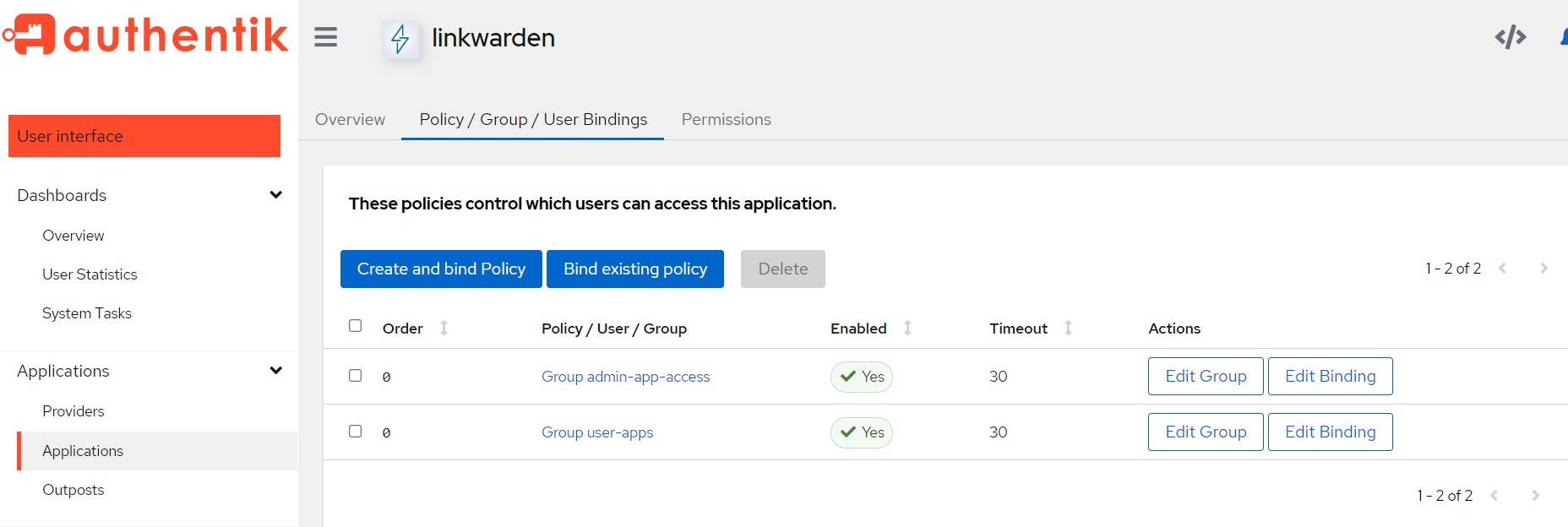
Finally, Assign users or groups of users to the application so they have access (Select the linkwarden application in Authentik, select the "Policy/Group/User Bindings" tab, then Bind existing Policy -> Group or users -> select either a group or a user):
Battle.net
The variables you need to configure to enable support for Battle.net (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_BATTLENET_ENABLED | - | If set to true, Battle.net will be enabled and you'll need to define the variables below. |
| BATTLENET_CUSTOM_NAME | - | Optionally set a custom provider name. |
| BATTLENET_ISSUER | - | Issuer. |
| BATTLENET_CLIENT_ID | - | Client ID |
| BATTLENET_CLIENT_SECRET | - | Client Secret. |
Box
The variables you need to configure to enable support for Box (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_BOX_ENABLED | - | If set to true, Box will be enabled and you'll need to define the variables below. |
| BOX_CUSTOM_NAME | - | Optionally set a custom provider name. |
| BOX_ISSUER | - | Issuer. |
| BOX_CLIENT_ID | - | Client ID |
| BOX_CLIENT_SECRET | - | Client Secret. |
Bungie
The variables you need to configure to enable support for Bungie (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_BUNGIE_ENABLED | - | If set to true, Bungie will be enabled and you'll need to define the variables below. |
| BUNGIE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| BUNGIE_API_KEY | - | API Key. |
| BUNGIE_CLIENT_ID | - | Client ID |
| BUNGIE_CLIENT_SECRET | - | Client Secret. |
Cognito
The variables you need to configure to enable support for Cognito (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_COGNITO_ENABLED | - | If set to true, Cognito will be enabled and you'll need to define the variables below. |
| COGNITO_CUSTOM_NAME | - | Optionally set a custom provider name. |
| COGNITO_ISSUER | - | Issuer. |
| COGNITO_CLIENT_ID | - | Client ID |
| COGNITO_CLIENT_SECRET | - | Client Secret. |
Coinbase
The variables you need to configure to enable support for Coinbase (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_COINBASE_ENABLED | - | If set to true, Coinbase will be enabled and you'll need to define the variables below. |
| COINBASE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| COINBASE_CLIENT_ID | - | Client ID |
| COINBASE_CLIENT_SECRET | - | Client Secret. |
Discord
The variables you need to configure to enable support for Discord (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_DISCORD_ENABLED | - | If set to true, Discord will be enabled and you'll need to define the variables below. |
| DISCORD_CUSTOM_NAME | - | Optionally set a custom provider name. |
| DISCORD_CLIENT_ID | - | Client ID |
| DISCORD_CLIENT_SECRET | - | Client Secret. |
Dropbox
The variables you need to configure to enable support for Dropbox (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_DROPBOX_ENABLED | - | If set to true, Dropbox will be enabled and you'll need to define the variables below. |
| DROPBOX_CUSTOM_NAME | - | Optionally set a custom provider name. |
| DROPBOX_CLIENT_ID | - | Client ID |
| DROPBOX_CLIENT_SECRET | - | Client Secret. |
Duende Identity Server 6
The variables you need to configure to enable support for Duende Identity Server 6 (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_DUENDE_IDS6_ENABLED | - | If set to true, Duende Identity Server 6 will be enabled and you'll need to define the variables below. |
| DUENDE_IDS6_CUSTOM_NAME | - | Optionally set a custom provider name. |
| DUENDE_IDS6_ISSUER | - | Issuer. |
| DUENDE_IDS6_CLIENT_ID | - | Client ID |
| DUENDE_IDS6_CLIENT_SECRET | - | Client Secret. |
EVE Online
The variables you need to configure to enable support for EVE Online (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_EVEONLINE_ENABLED | - | If set to true, EVE Online will be enabled and you'll need to define the variables below. |
| EVEONLINE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| EVEONLINE_CLIENT_ID | - | Client ID |
| EVEONLINE_CLIENT_SECRET | - | Client Secret. |
Facebook
The variables you need to configure to enable support for Facebook (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FACEBOOK_ENABLED | - | If set to true, Facebook will be enabled and you'll need to define the variables below. |
| FACEBOOK_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FACEBOOK_CLIENT_ID | - | Client ID |
| FACEBOOK_CLIENT_SECRET | - | Client Secret. |
FACEIT
The variables you need to configure to enable support for FACEIT (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FACEIT_ENABLED | - | If set to true, FACEIT will be enabled and you'll need to define the variables below. |
| FACEIT_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FACEIT_CLIENT_ID | - | Client ID |
| FACEIT_CLIENT_SECRET | - | Client Secret. |
Foursquare
The variables you need to configure to enable support for Foursquare (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FOURSQUARE_ENABLED | - | If set to true, Foursquare will be enabled and you'll need to define the variables below. |
| FOURSQUARE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FOURSQUARE_APIVERSION | - | API Version. |
| FOURSQUARE_CLIENT_ID | - | Client ID |
| FOURSQUARE_CLIENT_SECRET | - | Client Secret. |
Freshbooks
The variables you need to configure to enable support for Freshbooks (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FRESHBOOKS_ENABLED | - | If set to true, Freshbooks will be enabled and you'll need to define the variables below. |
| FRESHBOOKS_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FRESHBOOKS_CLIENT_ID | - | Client ID |
| FRESHBOOKS_CLIENT_SECRET | - | Client Secret. |
Fusionauth
The variables you need to configure to enable support for Fusionauth (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_FUSIONAUTH_ENABLED | - | If set to true, Fusionauth will be enabled and you'll need to define the variables below. |
| FUSIONAUTH_CUSTOM_NAME | - | Optionally set a custom provider name. |
| FUSIONAUTH_ISSUER | - | Issuer. |
| FUSIONAUTH_CLIENT_ID | - | Client ID |
| FUSIONAUTH_CLIENT_SECRET | - | Client Secret. |
| FUSIONAUTH_TENANT_ID | - | Tenant ID. |
Github
The variables you need to configure to enable support for Github (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_GITHUB_ENABLED | - | If set to true, Github will be enabled and you'll need to define the variables below. |
| GITHUB_CUSTOM_NAME | - | Optionally set a custom provider name. |
| GITHUB_CLIENT_ID | - | Client ID |
| GITHUB_CLIENT_SECRET | - | Client Secret. |
Gitlab
The variables you need to configure to enable support for Gitlab (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_GITLAB_ENABLED | - | If set to true, Gitlab will be enabled and you'll need to define the variables below. |
| GITLAB_CUSTOM_NAME | - | Optionally set a custom provider name. |
| GITLAB_CLIENT_ID | - | Client ID |
| GITLAB_CLIENT_SECRET | - | Client Secret. |
Google
The variables you need to configure to enable support for Google (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_GOOGLE_ENABLED | - | If set to true, Google will be enabled and you'll need to define the variables below. |
| GOOGLE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| GOOGLE_CLIENT_ID | - | Client ID |
| GOOGLE_CLIENT_SECRET | - | Client Secret. |
Hubspot
The variables you need to configure to enable support for Hubspot (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_HUBSPOT_ENABLED | - | If set to true, Hubspot will be enabled and you'll need to define the variables below. |
| HUBSPOT_CUSTOM_NAME | - | Optionally set a custom provider name. |
| HUBSPOT_CLIENT_ID | - | Client ID |
| HUBSPOT_CLIENT_SECRET | - | Client Secret. |
IdentityServer4
The variables you need to configure to enable support for IdentityServer4 (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_IDS4_ENABLED | - | If set to true, IdentityServer4 will be enabled and you'll need to define the variables below. |
| IDS4_CUSTOM_NAME | - | Optionally set a custom provider name. |
| IDS4_ISSUER | - | Issuer. |
| IDS4_CLIENT_ID | - | Client ID |
| IDS4_CLIENT_SECRET | - | Client Secret. |
Kakao
The variables you need to configure to enable support for Kakao (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_KAKAO_ENABLED | - | If set to true, Kakao will be enabled and you'll need to define the variables below. |
| KAKAO_CUSTOM_NAME | - | Optionally set a custom provider name. |
| KAKAO_CLIENT_ID | - | Client ID |
| KAKAO_CLIENT_SECRET | - | Client Secret. |
Keycloak
The variables you need to configure to enable support for Keycloak (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_KEYCLOAK_ENABLED | - | If set to true, Keycloak will be enabled and you'll need to define the variables below. |
| KEYCLOAK_CUSTOM_NAME | - | Optionally set a custom provider name. |
| KEYCLOAK_ISSUER | - | Issuer should include the realm – e.g. https://my-keycloak-domain.com/realms/My_Realm |
| KEYCLOAK_CLIENT_ID | - | The Keycloak client-id - can be obtained from Keycloak. |
| KEYCLOAK_CLIENT_SECRET | - | Can be obtained from Keycloak. |
Line
The variables you need to configure to enable support for Line (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_LINE_ENABLED | - | If set to true, Line will be enabled and you'll need to define the variables below. |
| LINE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| LINE_CLIENT_ID | - | Client ID |
| LINE_CLIENT_SECRET | - | Client Secret. |
Linkedin
The variables you need to configure to enable support for Linkedin (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_LINKEDIN_ENABLED | - | If set to true, Linkedin will be enabled and you'll need to define the variables below. |
| LINKEDIN_CUSTOM_NAME | - | Optionally set a custom provider name. |
| LINKEDIN_CLIENT_ID | - | Client ID |
| LINKEDIN_CLIENT_SECRET | - | Client Secret. |
Mailchimp
The variables you need to configure to enable support for Mailchimp (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_MAILCHIMP_ENABLED | - | If set to true, Mailchimp will be enabled and you'll need to define the variables below. |
| MAILCHIMP_CUSTOM_NAME | - | Optionally set a custom provider name. |
| MAILCHIMP_CLIENT_ID | - | Client ID |
| MAILCHIMP_CLIENT_SECRET | - | Client Secret. |
Mailru
The variables you need to configure to enable support for Mailru (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_MAILRU_ENABLED | - | If set to true, Mailru will be enabled and you'll need to define the variables below. |
| MAILRU_CUSTOM_NAME | - | Optionally set a custom provider name. |
| MAILRU_CLIENT_ID | - | Client ID |
| MAILRU_CLIENT_SECRET | - | Client Secret. |
Naver
The variables you need to configure to enable support for Naver (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_NAVER_ENABLED | - | If set to true, Naver will be enabled and you'll need to define the variables below. |
| NAVER_CUSTOM_NAME | - | Optionally set a custom provider name. |
| NAVER_CLIENT_ID | - | Client ID |
| NAVER_CLIENT_SECRET | - | Client Secret. |
Netlify
The variables you need to configure to enable support for Netlify (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_NETLIFY_ENABLED | - | If set to true, Netlify will be enabled and you'll need to define the variables below. |
| NETLIFY_CUSTOM_NAME | - | Optionally set a custom provider name. |
| NETLIFY_CLIENT_ID | - | Client ID |
| NETLIFY_CLIENT_SECRET | - | Client Secret. |
Okta
The variables you need to configure to enable support for Okta (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_OKTA_ENABLED | - | If set to true, Okta will be enabled and you'll need to define the variables below. |
| OKTA_CUSTOM_NAME | - | Optionally set a custom provider name. |
| OKTA_ISSUER | - | Issuer. |
| OKTA_CLIENT_ID | - | Client ID |
| OKTA_CLIENT_SECRET | - | Client Secret. |
Onelogin
The variables you need to configure to enable support for Onelogin (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_ONELOGIN_ENABLED | - | If set to true, Onelogin will be enabled and you'll need to define the variables below. |
| ONELOGIN_CUSTOM_NAME | - | Optionally set a custom provider name. |
| ONELOGIN_ISSUER | - | Issuer. |
| ONELOGIN_CLIENT_ID | - | Client ID |
| ONELOGIN_CLIENT_SECRET | - | Client Secret. |
Osso
The variables you need to configure to enable support for Osso (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_OSSO_ENABLED | - | If set to true, Osso will be enabled and you'll need to define the variables below. |
| OSSO_CUSTOM_NAME | - | Optionally set a custom provider name. |
| OSSO_ISSUER | - | Issuer. |
| OSSO_CLIENT_ID | - | Client ID |
| OSSO_CLIENT_SECRET | - | Client Secret. |
osu!
The variables you need to configure to enable support for osu! (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_OSU_ENABLED | - | If set to true, osu! will be enabled and you'll need to define the variables below. |
| OSU_CUSTOM_NAME | - | Optionally set a custom provider name. |
| OSU_CLIENT_ID | - | Client ID |
| OSU_CLIENT_SECRET | - | Client Secret. |
Patreon
The variables you need to configure to enable support for Patreon (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_PATREON_ENABLED | - | If set to true, Patreon will be enabled and you'll need to define the variables below. |
| PATREON_CUSTOM_NAME | - | Optionally set a custom provider name. |
| PATREON_CLIENT_ID | - | Client ID |
| PATREON_CLIENT_SECRET | - | Client Secret. |
Pinterest
The variables you need to configure to enable support for Pinterest (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_PINTEREST_ENABLED | - | If set to true, Pinterest will be enabled and you'll need to define the variables below. |
| PINTEREST_CUSTOM_NAME | - | Optionally set a custom provider name. |
| PINTEREST_CLIENT_ID | - | Client ID |
| PINTEREST_CLIENT_SECRET | - | Client Secret. |
Pipedrive
The variables you need to configure to enable support for Pipedrive (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_PIPEDRIVE_ENABLED | - | If set to true, Pipedrive will be enabled and you'll need to define the variables below. |
| PIPEDRIVE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| PIPEDRIVE_CLIENT_ID | - | Client ID |
| PIPEDRIVE_CLIENT_SECRET | - | Client Secret. |
Reddit
The variables you need to configure to enable support for Reddit (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_REDDIT_ENABLED | - | If set to true, Reddit will be enabled and you'll need to define the variables below. |
| REDDIT_CUSTOM_NAME | - | Optionally set a custom provider name. |
| REDDIT_CLIENT_ID | - | Client ID |
| REDDIT_CLIENT_SECRET | - | Client Secret. |
Salesforce
The variables you need to configure to enable support for Salesforce (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_SALESFORCE_ENABLED | - | If set to true, Salesforce will be enabled and you'll need to define the variables below. |
| SALESFORCE_CUSTOM_NAME | - | Optionally set a custom provider name. |
| SALESFORCE_CLIENT_ID | - | Client ID |
| SALESFORCE_CLIENT_SECRET | - | Client Secret. |
Slack
The variables you need to configure to enable support for Slack (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_SLACK_ENABLED | - | If set to true, Slack will be enabled and you'll need to define the variables below. |
| SLACK_CUSTOM_NAME | - | Optionally set a custom provider name. |
| SLACK_CLIENT_ID | - | Client ID |
| SLACK_CLIENT_SECRET | - | Client Secret. |
Spotify
The variables you need to configure to enable support for Spotify (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_SPOTIFY_ENABLED | - | If set to true, Spotify will be enabled and you'll need to define the variables below. |
| SPOTIFY_CUSTOM_NAME | - | Optionally set a custom provider name. |
| SPOTIFY_CLIENT_ID | - | Client ID |
| SPOTIFY_CLIENT_SECRET | - | Client Secret. |
Strava
The variables you need to configure to enable support for Strava (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_STRAVA_ENABLED | - | If set to true, Strava will be enabled and you'll need to define the variables below. |
| STRAVA_CUSTOM_NAME | - | Optionally set a custom provider name. |
| STRAVA_CLIENT_ID | - | Client ID |
| STRAVA_CLIENT_SECRET | - | Client Secret. |
Todoist
The variables you need to configure to enable support for Todoist (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_TODOIST_ENABLED | - | If set to true, Todoist will be enabled and you'll need to define the variables below. |
| TODOIST_CUSTOM_NAME | - | Optionally set a custom provider name. |
| TODOIST_CLIENT_ID | - | Client ID |
| TODOIST_CLIENT_SECRET | - | Client Secret. |
Twitch
The variables you need to configure to enable support for Twitch (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_TWITCH_ENABLED | - | If set to true, Twitch will be enabled and you'll need to define the variables below. |
| TWITCH_CUSTOM_NAME | - | Optionally set a custom provider name. |
| TWITCH_CLIENT_ID | - | Client ID |
| TWITCH_CLIENT_SECRET | - | Client Secret. |
United Effects
The variables you need to configure to enable support for United Effects (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_UNITED_EFFECTS_ENABLED | - | If set to true, United Effects will be enabled and you'll need to define the variables below. |
| UNITED_EFFECTS_CUSTOM_NAME | - | Optionally set a custom provider name. |
| UNITED_EFFECTS_ISSUER | - | Issuer. |
| UNITED_EFFECTS_CLIENT_ID | - | Client ID |
| UNITED_EFFECTS_CLIENT_SECRET | - | Client Secret. |
VK
The variables you need to configure to enable support for VK (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_VK_ENABLED | - | If set to true, VK will be enabled and you'll need to define the variables below. |
| VK_CUSTOM_NAME | - | Optionally set a custom provider name. |
| VK_CLIENT_ID | - | Client ID |
| VK_CLIENT_SECRET | - | Client Secret. |
Wikimedia
The variables you need to configure to enable support for Wikimedia (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_WIKIMEDIA_ENABLED | - | If set to true, Wikimedia will be enabled and you'll need to define the variables below. |
| WIKIMEDIA_CUSTOM_NAME | - | Optionally set a custom provider name. |
| WIKIMEDIA_CLIENT_ID | - | Client ID |
| WIKIMEDIA_CLIENT_SECRET | - | Client Secret. |
Wordpress.com
The variables you need to configure to enable support for Wordpress.com (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_WORDPRESS_ENABLED | - | If set to true, Wordpress.com will be enabled and you'll need to define the variables below. |
| WORDPRESS_CUSTOM_NAME | - | Optionally set a custom provider name. |
| WORDPRESS_CLIENT_ID | - | Client ID |
| WORDPRESS_CLIENT_SECRET | - | Client Secret. |
Yandex
The variables you need to configure to enable support for Yandex (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_YANDEX_ENABLED | - | If set to true, Yandex will be enabled and you'll need to define the variables below. |
| YANDEX_CUSTOM_NAME | - | Optionally set a custom provider name. |
| YANDEX_CLIENT_ID | - | Client ID |
| YANDEX_CLIENT_SECRET | - | Client Secret. |
Zitadel
The variables you need to configure to enable support for Zitadel (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_ZITADEL_ENABLED | - | If set to true, Zitadel will be enabled and you'll need to define the variables below. |
| ZITADEL_CUSTOM_NAME | - | Optionally set a custom provider name. |
| ZITADEL_ISSUER | - | Issuer. |
| ZITADEL_CLIENT_ID | - | Client ID |
| ZITADEL_CLIENT_SECRET | - | Client Secret. |
Zoho
The variables you need to configure to enable support for Zoho (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_ZOHO_ENABLED | - | If set to true, Zoho will be enabled and you'll need to define the variables below. |
| ZOHO_CUSTOM_NAME | - | Optionally set a custom provider name. |
| ZOHO_CLIENT_ID | - | Client ID |
| ZOHO_CLIENT_SECRET | - | Client Secret. |
Zoom
The variables you need to configure to enable support for Zoom (OIDC):
| Environment Variable | Default | Description |
|---|---|---|
| NEXT_PUBLIC_ZOOM_ENABLED | - | If set to true, Zoom will be enabled and you'll need to define the variables below. |
| ZOOM_CUSTOM_NAME | - | Optionally set a custom provider name. |
| ZOOM_CLIENT_ID | - | Client ID |
| ZOOM_CLIENT_SECRET | - | Client Secret. |
Addons
Install as a PWA (ProgressiveWebApp)
Install Linkwarden as a Progressive Web App (PWA) on your phone, tablet, or computer to use it like a native app without needing an app store download.
A PWA functions like a traditional app but is installed directly from the website onto your device.
Installation
iOS
-
Open cloud.linkwarden.app in Safari. Or if you're self-hosting, open your instance's URL.
-
Tap the Share button at the bottom of the screen.
-
Tap the Add to Home Screen icon in the Share menu.
-
Tap Add in the upper-right corner.
You can also get the iOS Shortcut to quickly add links to Linkwarden from the share sheet on iOS. Click here to learn more.
 |
 |
 |
Android
-
Open cloud.linkwarden.app in Chrome. Or if you're self-hosting, open your instance's URL.
-
Press the three dots in the upper-right corner to open the menu.
-
Tap Add to Home Screen.
-
Tap Add in the pop-up.
Chrome (Desktop)
-
Open cloud.linkwarden.app in Chrome. Or if you're self-hosting, open your instance's URL.
-
Click the Install icon in the right side of the address bar.
-
Click Install in the pop-up.
 |
Linkwarden Browserextension
Extension for Linkwarden, a self-hosted, open-source collaborative bookmark manager to collect, organize and archive webpages.
Features
- Add and organize new links to Linkwarden with a single click.